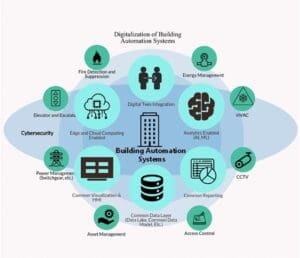
In the world of supply chain and logistics, the built environment comes in many forms, from warehouses and logistics parks to the buildings associated with ports and terminals. The IT realm spends a significant amount on cybersecurity and there are many large suppliers that provide solutions for cybersecurity at the IT and enterprise level. The operational technology (OT) world, however, is a different story. Most owner operators do not have a good picture of the OT assets in their built environment.
These assets are significant in size and scope, and include proprietary, purpose-built building automation systems that control things like HVAC, lighting, building energy management, fire detection and suppression, and security systems like access control and CCTV. Each of these systems features their own attached sensors and devices, from cameras to thermostats to light sensors. Having good asset visibility and a good understanding of the cybersecurity posture of your installed base of OT assets can be just as important for buildings as it is for the many operational and enterprise technologies that impact the supply chain.
The Cyber Risks of Building Automation Systems: The Target Hack
If you don’t think cybersecurity for the built environment is a risk, consider the well-publicized cyber attack on major retailer Target back in 2013. Target allowed a third party HVAC vendor access to their networks, where the vendor remotely monitored the operating state of the building automation systems at multiple Target locations. The third party vendor, however, was breached by an attacker, who then used the vendor’s remote access privileges to breach Target’s network. The attacker then moved laterally through Target’s network, eventually installing malware on point of sale (POS) terminals, which then scraped the customer financial data of over 40 million credit and debit card accounts.
From the obscure world of HVAC controls to financial systems in a few simple steps, the incident is still one of the largest data breaches in history and a great illustration of how nothing is truly isolated or “air gapped” anymore. It’s also a great example of how the boundaries between what we traditional think of as “IT” and “OT” cybersecurity are blurring. An attack at the OT level can have significant consequences for the enterprise IT level and vice versa.
Why Building Automation System Cybersecurity is Neglected
Despite the ongoing risks and lessons of the past, many end users in the warehousing and logistics space have not yet fully evaluated the security of their built environment and have an incomplete picture of its overall security posture and resilience. Compared to the world of industrial control systems (ICS), which in supply chain includes things like robotics, material handling systems, and AGVs, the domain of building automation tends to have less OT level security expertise and an overall lower adoption rate of accepted cybersecurity frameworks and standards such as ISO 27000, NIST CSF, ISA/IEC 62443, and CIS Controls.
Many warehouses don’t even have dedicated OT networks, and that includes the built infrastructure. Often, the OT assets associated with building automation and other OT related functions are on the same networks as IT and enterprise systems. As more digital technologies find their way into warehouses, it is becoming increasingly important to have dedicated OT networks that follow the proper rules of network segmentation and defense-in-depth, which are standard practices in the world of manufacturing.
New Building Automation Systems Expand the Threat Surface
Buildings require reliable 24-hour operation, and the move to new technologies such as industrial IoT, cloud computing, edge computing, and analytics is driving a shift to remote building management and monitoring. Adoption of new technologies like edge computing devices, intelligent sensors with wireless capabilities, smart lighting systems, and more is all creating a huge technology shift in the once relatively unchanging world of building automation. Most buildings today implement at least some aspect of “smart” technology or intelligence, even if it’s only wirelessly connected thermostats.
The big push to adopt IoT and remote connectivity has resulted in many connected buildings with remote access, but these remote connections are not always secure. Today’s integrated building automation systems can handle much more than just HVAC or energy management applications. New IoT-based architectures allow for just about any function in the built environment to be integrated into a single common system, with common visualization, common reporting functions, a single engineering environment, and more.
All this interconnectedness, however, raises increasing concerns about cybersecurity. Many supplier offerings lack an appropriate emphasis on cybersecurity, or they leave cybersecurity up to the end user, as a layer to be put on top of the system that is being purchased. Suppliers should have both secure development lifecycle with certified or registered products and host systems where possible. Suppliers can also offer additional options for OT level cybersecurity by forming alliances with leading OT level cybersecurity vendors.
Implementing Cybersecurity Programs for Buildings: Simple Steps
End users need to evaluate their risks by assessing likelihood and impact and then decide what actions, if any, are necessary to protect critical objectives like financial performance, safety, compliance, operational continuity, etc. This all starts with a cyber assessment of the built environment. Other basic foundational tasks for setting up a good cybersecurity program include doing a good asset inventory. Most end users and owner/operators find this to be an eye-opening exercise, as there are almost always rogue assets and other hitherto unknown assets lurking in OT networks, from insecure commercially available IP cameras to rogue wireless access points.
Looking at existing frameworks and standards is a good way to get started on an OT security program. A good place to start is NIST, the National Institute of Standards and Technology, which offers its cybersecurity framework (CSF) as well as many other resources, including quick start guides. CISA is the branch of DHS that handles critical infrastructure cybersecurity, and they have may resources as well, including free cybersecurity services. The ISA (International Society of Automation) and the International Electrotechnical Commission (IEC) publish and maintain the ISA/IEC 62443 set of cybersecurity standards, which is the primary cybersecurity standard used in the manufacturing sector worldwide, representing years of accrued knowledge and best practices in OT level cybersecurity.
Doing something is better than doing nothing. Start looking into your built environment and try to understand the potential cyber risks posed by it. You may be surprised at what you find.




















